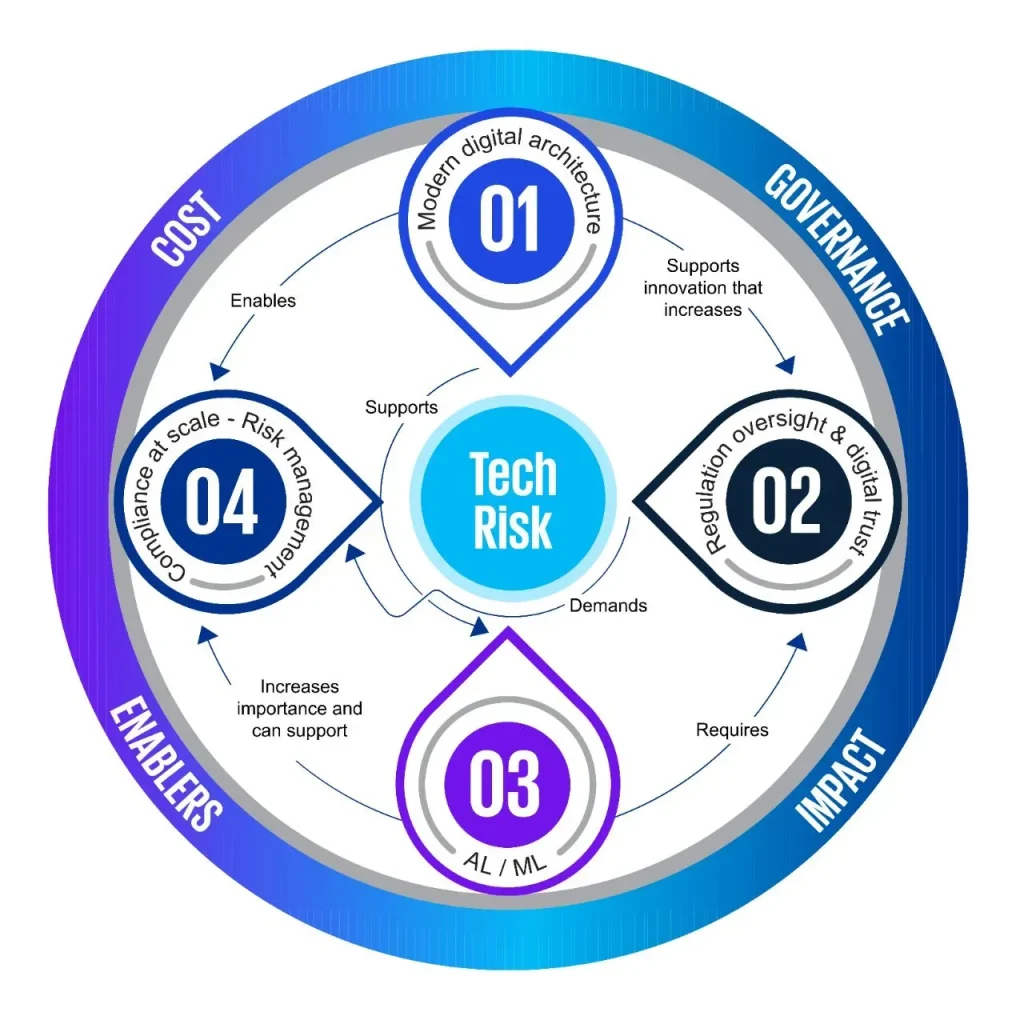
Technology risk management has shifted from a niche IT concern to a strategic discipline that protects value, trust, and resilience across the entire organization. As digital technologies permeate every function—from customer experiences to supply chains—the likelihood and impact of digital disruption risk rise, demanding proactive governance. A robust program helps leaders identify, assess, and mitigate risks before they become costly incidents. This approach aligns governance and risk activities with business goals through clear policies, executive sponsorship, and ongoing oversight. In practice, it connects technology risk assessment and cyber risk management with resilience efforts such as business continuity planning, enabling faster recovery and sustained trust.
Viewed through the lens of information technology risk oversight, the topic centers on safeguarding systems, data, and people against evolving threats. From this angle, organizations emphasize tech risk governance and operational resilience to prevent, detect, and respond to incidents. Other terms like IT risk management, digital risk governance, and information systems risk control reflect the same core objective: balancing risk with innovation. By framing risk in terms of business outcomes—customer trust, regulatory compliance, and supply-chain continuity—leaders can communicate strategy and secure cross-functional buy-in. A holistic, semantic approach helps teams tie technical risk to strategy, governance, and resilience so technology-enabled growth remains safe and sustainable.
Technology Risk Management: Designing Resilience Across the Organization
Technology risk management is a strategic discipline that protects value, trust, and resilience across all parts of the organization. It goes beyond IT silos to influence business outcomes, customer experience, and operational continuity. In an era of digital disruption risk, a well-structured program ensures leaders can identify, assess, and mitigate threats before they disrupt growth or erode credibility.
To design an effective approach, establish a governance framework that defines accountability, risk appetite, and decision rights for technology risk. A robust program integrates technology risk assessment into regular planning cycles, creates an accurate inventory of assets and data flows, and maps dependencies across vendors and platforms. The result is coordinated, board-facing reporting and a clear link between risk controls and strategic objectives.
Digital Disruption Risk: Proactively Identifying and Prioritizing Tech Threats
Digital disruption risk is not a theoretical concern; it’s a business reality driven by cloud, automation, AI, and mobile platforms. Viewing disruption as a core risk helps organizations anticipate outages, performance degradations, and data privacy incidents that could derail customer journeys and revenue streams. A proactive stance starts with a comprehensive technology risk assessment that prioritizes threats by impact and likelihood.
By mapping critical assets, data flows, and third-party dependencies, teams can target the most consequential vulnerabilities with prioritized mitigation. This approach aligns security investments with business goals, strengthens resilience, and supports faster recovery when disruptions occur. Integrating disruption scenarios into governance and testing ensures continuity planning remains ahead of evolving technology landscapes.
Cyber Risk Management and Governance: Integrating Security into Tech Decision-Making
Cyber risk management plays a central role in protecting data, identities, and systems from unauthorized access. When embedded in risk governance for technology, cyber controls support business objectives rather than acting as compliance checkboxes. This integrated view reduces siloed risk management and ensures cyber incidents are analyzed within the broader context of organizational risk.
Effective governance requires cross-functional collaboration among IT, security, risk, and business units, with clear escalation paths and regular board-level reporting. By tying cyber risk indicators to enterprise KRIs, organizations can monitor exposure, adjust risk appetite, and demonstrate resilience to customers and regulators. Continuous improvement comes from post-incident reviews, audits, and control testing that feed back into governance updates.
Business Continuity Planning as the Backbone of Tech Resilience
Business continuity planning is essential to sustaining critical operations during and after disruptions. A robust plan covers disaster recovery, backup strategies, alternate processing sites, and clearly defined recovery time objectives (RTOs) and recovery point objectives (RPOs). Integrating these elements into technology risk management helps preserve value, protect revenue, and maintain customer trust.
Resilience extends beyond technical outages to supply chain interruptions, third-party failures, and workforce disruptions. A comprehensive continuity program aligns with risk governance for technology, ensuring that recovery priorities reflect strategic goals and customer commitments. Regular testing and real-time simulations validate plans, highlight gaps, and promote faster, more predictable recovery.
Incident Response, Drills, and Continuous Improvement: Building Real-World Readiness
Incident response and recovery testing translate planning into action. A well-defined plan establishes roles, communication protocols, and escalation paths, while regular tabletop exercises and live drills simulate real incidents. The goal is rapid containment, accurate lessons learned, and continuous improvement of people, processes, and technology.
Embedding incident response into daily operations reinforces resilience. Runbooks, 24/7 alerting, and scenario-based training ensure teams can execute under pressure. Lessons learned feed back into technology risk assessment and governance updates, strengthening the organization’s ability to anticipate and respond to digital disruption risk with speed.
Vendor Risk Management and Third-Party Oversight in a Connected Ecosystem
In a highly connected environment, vendors can introduce significant risk. A formal vendor risk management program includes due diligence, continuous monitoring, contractually defined security and continuity obligations, and exit strategies. Effective oversight requires collaboration across procurement, security, and business units to ensure third parties meet risk tolerance and regulatory requirements.
Ongoing vendor evaluation should focus on reliability, data protection, and continuity capabilities of external partners, including cloud providers and payment processors. Integrating third-party risk considerations into technology risk governance helps ensure that vendor controls align with strategic objectives, protect customer data, and sustain operations even when external partners face disruptions.
Frequently Asked Questions
What is digital disruption risk in the context of Technology risk management, and why does it matter?
Digital disruption risk refers to threats from rapid technology changes or outages that can affect operations, customer experience, or revenue. In Technology risk management, you identify and prioritize this risk, assess its impact and likelihood, and implement governance, incident response, and business continuity planning to protect value and trust.
How does a Technology risk assessment address digital disruption risk?
A Technology risk assessment inventories information assets, applications, data flows, and vendors; it identifies vulnerabilities and dependencies, and scores risks to guide mitigation priorities. It should be ongoing, aligned with regulatory requirements and business goals, and inform where to invest in resilience measures.
How is cyber risk management integrated with business continuity planning within Technology risk management?
Cyber risk management protects data, identities, and systems from unauthorized access and is most effective when integrated with business continuity planning, ensuring critical operations can recover quickly after cyber incidents. This integration also ties incident response testing and recovery objectives to overall resilience.
What is risk governance for technology, and how does it sustain Technology risk management?
Risk governance for technology sets risk appetite, roles, accountabilities, and reporting structures; it ensures cross-functional ownership and board-level visibility. It enables consistent risk decisions and continuous improvement through clear policies, metrics, and lessons learned from incidents and audits.
Why is incident response testing important for cyber risk management within Technology risk management?
Incident response testing validates playbooks, roles, and escalation paths, enabling faster containment and better decision-making during events. Regular drills reveal gaps in people, processes, and technology, driving continual improvement in both cyber risk management and Technology risk management.
How should an organization begin implementing a Technology risk management program, including risk governance for technology and technology risk assessment?
Start with a centralized risk register and taxonomy, map data flows, and establish an initial vendor risk program. Define risk governance for technology, articulate risk appetite, and perform a technology risk assessment to prioritize controls and resilience investments, then iterate with ongoing monitoring and governance enhancements.
| Area | Key Points | Notes / Examples |
|---|---|---|
| Definition | Technology risk management is the systematic process to identify, evaluate, and control risks from technology across people, processes, data, and systems; goal is to reduce risk to an acceptable level while enabling innovation. | Threats include cyberattacks, system failures, third-party dependencies, data privacy concerns, and regulatory changes. |
| Why Digital Disruptions Matter | Digital disruption risk is a business risk driven by rapid tech adoption; requires planning, testing, and ongoing governance to reduce recovery time and protect revenue and trust. | Outages can disrupt customer journeys, manufacturing, or expose sensitive data. |
| Governance | Strong governance establishes rules, ownership, risk appetite, policies, and procedures; assigns ownership across units; ensures executive sponsorship and board reporting. | Supports consistent risk decisions and measurement. |
| Risk Assessment & Inventory | Inventory of information assets, applications, data flows, vendors, and infrastructure; regular audits; ongoing discipline; align with regulations and business goals; prioritize by impact/likelihood. | Identifies vulnerabilities, dependencies, and failure points. |
| Cyber Risk Integration | Protect data, identities, and systems; integrate with other risk domains to avoid silos. | Cyber controls support business objectives and are analyzed in the broader risk context. |
| Business Continuity & Resilience | Plan to maintain or quickly resume critical operations; include DR, backups, alternate sites, and recovery objectives. | Resilient against outages, supply chain interruptions, and workforce disruption. |
| Incident Response & Testing | Define roles, communication, escalation; conduct tabletop and live drills; validate responses and capture lessons. | Drills enable rapid containment and continuous improvement. |
| Vendor Risk & Third-Party Oversight | Due diligence, ongoing monitoring, contract obligations, and exit strategies; cross-functional collaboration. | Integrates vendor risk into the overall program. |
| Measurement & Improvement | Use metrics and KRIs; regular reporting to executives and board; feedback loops; refine controls and governance. | Examples include mean time to detect, incident costs, and recovery time. |
| Practical Strategies (Selected) | Develop a Risk Register; map data flows; implement layered controls; invest based on risk; embed incident response; foster risk awareness; align with business strategy. | Highlights actions and sequencing from the practical section. |
| Case in Point | Retailer example focusing on e-commerce peak season: risk assessment, cyber controls, BC planning, incident response, vendor risk, and governance refinement. | Emphasizes safeguarding customer experience. |
Summary
HTML table provided summarizes key points of Technology risk management from the base content, followed by a descriptive conclusion.